A methodology for architecture-oriented rapid prototyping
Abstract
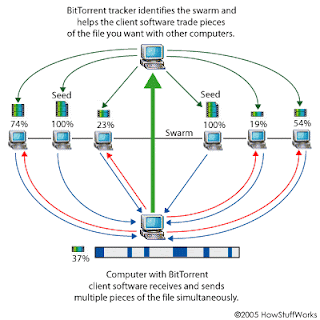
A methodology for architecture-oriented rapid prototyping is presented. In the very early development phases, concept-oriented rapid prototyping is used to clarify the requirements between the customer and the contractor. In the second, more complex phase of rapid prototyping, the architecture of the target system is used. So this kind of rapid prototyping is called “architecture-oriented rapid prototyping”. Most electronic control units (ECUs) use microcontrollers with plenty of on-chip peripherals. Sometimes, application-specific microcontrollers with non-standard peripherals are used, but then, all of these peripheral components must be present in the rapid prototyping system. To obtain this, we developed an interface module with an FPGA for the peripheral parts of microcontroller-based designs, as well as a prototyping ECU which can be programmed with CASE tools